CORE ELEMENTS OF NETWORKING
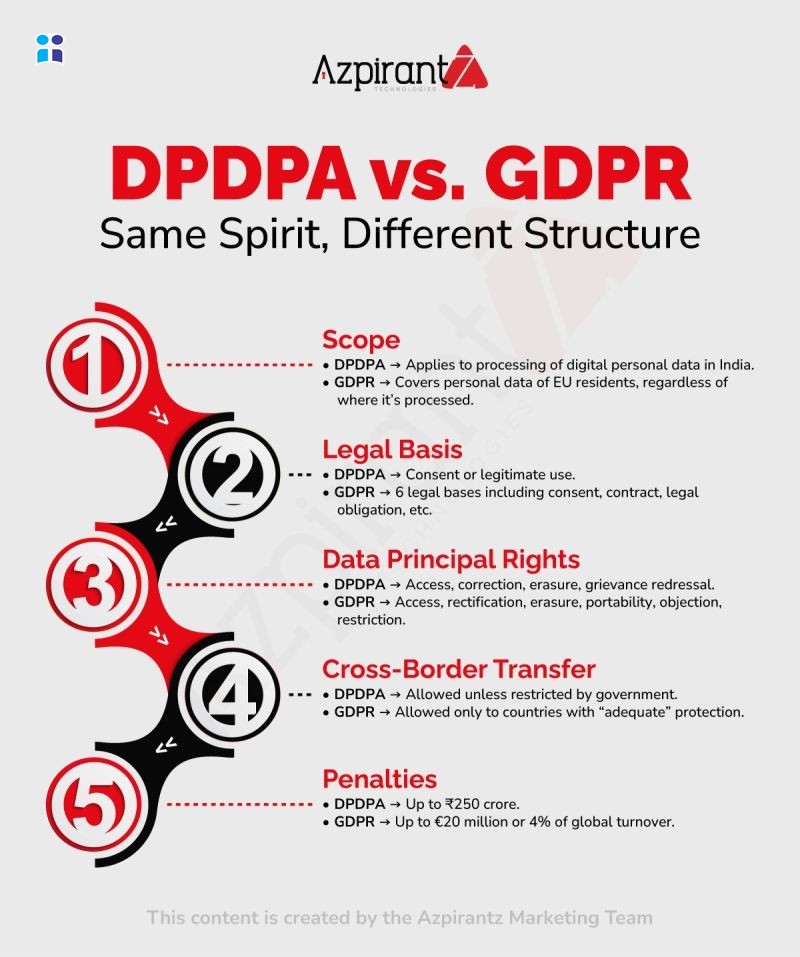
This infographic breaks down the core elements of networking, highlighting key components that keep modern networks functioning efficiently. It covers switches that connect devices internally, routers that move data between networks, VLANs that segment traffic, trunking for carrying multiple VLANs, STP for preventing loops, ACLs for controlling access, and EtherChannel for boosting speed and redundancy. A quick, practical guide for learners and professionals strengthening their networking fundamentals.
#networking #switches #routers #vlan #trunking #stp #acl #etherchannel #networkfundamentals